Posted on June 20, 2019
My OSCP transformation – 2019 | Write-up [2023 Update]
The recent months have significantly reshaped me in numerous ways. The days and nights I dedicated to trying to root Offsec’s Lab machines will forever be etched in my memory. Without question, this has been the most challenging obstacle I’ve ever encountered in my professional journey.
Going through a complete spectrum of emotions, including excitement, aggravation, joy, and satisfaction, has shown to be quite beneficial in improving my general cybersecurity skills.

Conclusion: Try harder smarter.
My background:
I spent the last 5 years working in several SOCs/CSIRTs as a Security Analyst. Blue Team to the bone. Here’s what I knew before passing the OSCP:
- Basic Linux and Windows CLI skills
- Scripting, basic to good skills with: Power-Shell, Python, C, PHP, C#, SQL
- SIEM: IBM QRadar , RSA Netwitness , Splunk, Graylog, Elasticsearch, Kibana
- GRC/ Incident Response Solutions: RSA Archer SECOPS, Redmine, OTRS
- Malware Analysis: Wireshark, IDA, X64dbg, Microsoft Sysinternals, Cuckoo
- Vulnerability assessment: Nmap, Qualys, Nessus, Shodan
I also hold several security related certifications. I will add a small description next to each certification so you can understand its use:
- SANS GCIH (504) : GIAC Certified Incident Handler: Manage security incidents by understanding common attack techniques, vectors and tools as well as defending against and/or responding to such attacks when they occur. Methods used to detect, respond, and resolve computer security incidents.
- SANS GREM (610) : GIAC Reverse Engineering Malware: Possess the knowledge and skills to reverse-engineer malicious software (malware) that targets common platforms, such as Microsoft Windows and web browsers. Know how to examine inner-workings of malware in the context of forensic investigations, incident response, and Windows system administration.
- ISO/IEC 27002 ISO Information Security foundations: Information and security, Threats and risks, Approach and organization, Measures, Legislation and regulation.
My OSCP Journey:
Chronology:
- March 1st: made my order on with two months of Lab time.
- March 24th: got the access to the labs and course materials. I started doing the exercices while reading the PDF and watching the videos.
- April 7th: started the lab.
- May 5th: one month extension as I hadn’t finished all of the Lab machines.
- June 6th: stopped doing the labs after rooting almost all of the Lab machines including the big 4.
- June 11th: scheduled my exam.
- June 14th 23h: exam.
- June 16th 22h: submitted exam and Lab reports.
- June 19th 16h25: got the results from Offsec: PASSED!
Takeaways:
- Labs:
- Don’t boycott the forums. Go there if you’re really, really stuck. You’re going to be less and less dependant as you gain more experience through the labs.
- Do the Lab exercices. I can’t emphasize this enough: it will really help you understand the “Offsec’s” way of doing penetration testing.
- Always revert the machine before starting. Duh..
- Build your customized penetration testing framework/checklist. You should have a first prototype once you root your first 5-10 machines.
- Metasploit/Meterpreter: I used it a few times in the Labs when I started and then stopped using it completely. You don’t really need metasploit in the Lab machines. It’s faster to use the meterpreter for dumping passwords and elevating privileges but it can lead you to miss a lot of interesting skills.
- When searching for exploits, look if the exploit comes more than once in your searches. If this the case, you should prioritise that exploit.
- Exploits that run locally, on a victim machine, most commonly exploit a process or service with higher privileges.
- Sometimes, no checklist/enumeration script will work. Not even g0tm1lk’s or FuzzySecurity’s guides. You have to dig deep and manually search for interesting findings. Take a deep breath, assess the situation from a global point of view and then try smarter.
- Always try manual/service exploits before using kernel exploits which should really be your last resort.
- You’ll often need to modify exploit code. You’ll rarely find an exploit code on EDB that works out of the box.
- Enumerate installed patches on Windows before trying the kernel exploits.
- Post exploitation/Low priv shell: you should be able to confirm any data/information gathered remotely as you now have local access to the box (if it doesn’t match up – why!).
- Look for users in
/etc/passwdand try to login using them. - Some services require to be port-forwarded to your machine in order to be attacked.
- There’s a few automate scripts which can be used to help out. These will produce a lot of “data”, which you will need to convert into “meaningful” information.
- Always upgrade your shell as much as you can.
- Pivoting can be hard.. but God then created “sshuttle“.
- Do your post-exploitation routine and harvest every valuable piece of information: passwords, hashes, usernames and other interesting artifacts.
- Backup your Kali VM every now and then.
- Recommended books over here.
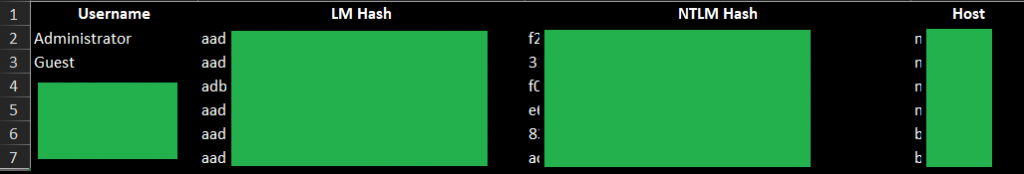
- I put together an index with every looted password/account:
- Reporting:
- I tried CherryTree and KeepNote but I preferred to use OneNote because I used several PC’s to work. Data is kept safe and up to date in the cloud. The new Dark theme made it a far more satisfying experience.
SHIFT + Win + Sto take screenshots in Windows 10.- I used tools like Reconnoitre and Faraday for information gathering and service enumeration but I soon got back to copying pasting output directly to OneNote. A typical machine report in OneNote would like this:

- Exam preparation:
- I did a 24 hours pre-exam exercise with machines I download from Vulnhub the weekend before the exam date. You can download the virtual machines from here.
- Here’s a great resource for Buffer Overflow. Do it again and again until you understand every step of the process.
- I read a countless amount of blog posts on exam preparation. I will put the links over here.
- I also created an index that identified the root method that I used on every Lab machine. It can help during the exam or other Lab machines when encountering similar vulnerabilities. Here’s a sample of my index:

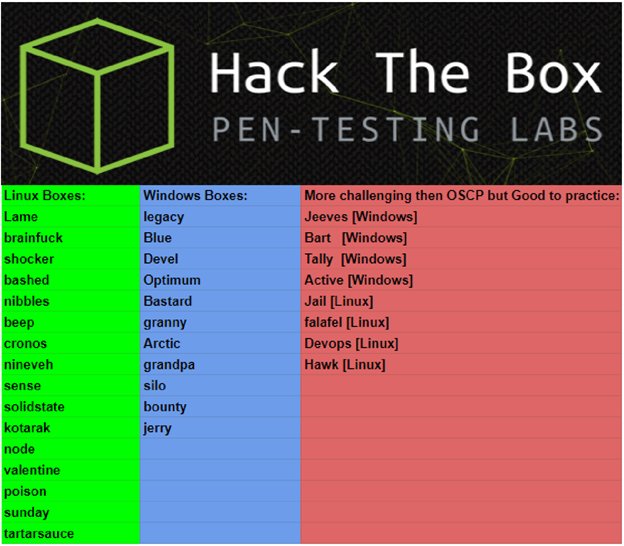
- I did some Hack The Box machines. Most of the HTB medium difficulty machines are harder than Offsec Lab machines. Here’s some HTB machines that look like Offsec’s Lab machines:
- Exam:
- Note that I passed from the first attempt 🙂 I managed to get 3/5 machines + 1 low privilege shell on the 4th machine.
- My Kali VM was pretty stable for the entire 3 months Lab period. However, while doing the exam, and after 12 hours of work and numerous open terminator tabs, my VM decided to crash 😀 I recommend taking multiple snapshots of your VM while doing the exam to not lose everything.
Of course, use OBS Studio to record your screen. It helped me on multiple occasions when I was writing my post-exam report.PWK has officialy banned screen recording during the exam.- No stress whatsoever. Take your time, enumerate all services, make notes of enumerated software/service versions and every information you discover. Save everything into OneNote.
- When you’re stuck, take a step back and check your notes on OneNote. Enumerate more.
- BFO should take you 1h. It took me 2h30 because I missed something. Make a solid BFO checklist before the exam.
- I used a script called nmapAutomator to launch enumeration scripts. It worked like a charm.
- Never spend more than 2-3 hours on one machine. If you’re stuck, move on to the next machine.
- Drink a lot of water and eat low sugar, high fat food (nuts, fish, whole wheat bread).
- My friend gave me a couple of caffeine pills. It really helped me when I hit a wall.
- Music: Deep Focus Spotify playlist is highly recommended! There are also several OSCP playlists that you can check out.
Please find my bookmarks here.
My Lab Setup:
There’s nothing extravagant about it. My workstation Battlestation may not be the latest model, but it’s certainly capable of running a virtual machine and over a hundred open tabs in Chrome/Firefox 😜
Here are the specs:
- CPU: Intel core I5 4590 @3.3 Ghz
- RAM: 20 Gb DDR3 1333 Mhz
- GPU: GTX 670 2Gb GDDR5
- Disk: 256 Gb SSD + 4 Tb HDD
- Display: Asus VA32AQ 32″ 2K + Samsung LS22E45UFS/EN 21,5” (vertical screen)
- Keyboard: Logitech G213 Prodigy
- Mouse: Logitech G500 – with infinite scroll 😉
Here’s what my setup looked like on the day of the exam:

My next desired certifications :
SANS 508- SANS 542/642
SANS 660- OSEP
- CISSP (I don’t know where to start, it’s so boring)
Thank you for reading my blog post. Please do not hesitate to contact me if you have any questions. You can also connect with me on Linkedin.
You can also find this article written in French HERE.

Great write-up dude!! taking it for my 5th time in a month. I would recommend adding haircut and October to that list of htb prep boxes as well.
This was extremely helpful. I have just finished the course material, and am sort of stuck now in the labs like a deer in headlights. Question: How did you get OneNote to work on Kali? I thought it wasn’t compatible!
I’m glad it helped 🙂
I didn’t run OneNote in Kali. I ran kali in Vmware Workstation on a Windows platform. I connected a second screen that was mostly dedicated to OneNote. Take a look at the photo that I provided, you can the second vertical screen that I used.